|
|
|
Cybersecurity was already a high growth profession, but the events of recent days have taken the importance of hardening cybersecurity to an entirely new level. So, the need for trained professionals has become a lot more real. In this issue, we provide pragmatic ideas and advice on how you can be an integral part of a rapidly accelerating cybersecurity movement through offering training in just a few, but important, areas.
Jim Gabalski
VP, Sales and Marketing
In this issue:
|
|
|
|
|
|
|
|
|
The Perfect Storm
by Jon O'Keefe, Technology Education Jedi
|
| |
|
The “Perfect Storm” in cybersecurity is upon us. I am predicting that over the next 18-24 months, the number of students seeking cybersecurity training is going to increase at a rate we’ve never seen before. This prediction is partly based on the following facts:
-
According to ISSA, the cybersecurity skills gap is worsening for the fifth straight year, and almost 75% of all organizations will face security issues because of this.
-
The Great Resignation is real. According to SHRM, almost four million people a month have quit their job, and this includes a growing number of cybersecurity professionals.
-
According to Forbes, suspected Russian cyber attacks went up 800% after the invasion of Ukraine
-
More than one million fewer students are going to college, continuing a historic decline in attendance according to NPR.
 We are living through a “Perfect Storm” of events for individuals who want to pursue cybersecurity careers. With the skills gap already worsening, many security professionals retiring or looking for other opportunities, and the new face of war being a potential massive cyber conflict, there has never been a better time to invest in your growth as a cybersecurity professional. If you look at all of that and combine it with the fact that fewer young people are going to college in lieu of getting vocational/certification training, you have the conditions for an explosion in cybersecurity training. We are living through a “Perfect Storm” of events for individuals who want to pursue cybersecurity careers. With the skills gap already worsening, many security professionals retiring or looking for other opportunities, and the new face of war being a potential massive cyber conflict, there has never been a better time to invest in your growth as a cybersecurity professional. If you look at all of that and combine it with the fact that fewer young people are going to college in lieu of getting vocational/certification training, you have the conditions for an explosion in cybersecurity training.
Your job in this explosive market is to figure out the best way to reach students, determine the best training to offer them that can help them quickly grow their skillset and find a job, and to make sure your instructors are prepared to be driving students forward from class to class, certification to certification.
The great news is that Logical Operations and CertNexus have been preparing for this for many years. We can help you with easy-to-teach, valuable skill-driven certifications in cybersecurity. We have marketing kits available (with more on the way) around some of the most in-demand topics in the industry. Finally, we can provide train-the-trainer opportunities to make sure your trainers are fully up to speed.
Don’t miss out on this once-in-a-generation moment in training; we’re here to help you take advantage of this amazing opportunity!
|
|
|
|
|
Sell into the Cybersecurity Triangle
by Jim Gabalski, VP, Sales and Marketing
|
| |
|
A triangle has long been used to represent a market opportunity, and this is true when you think about the cybersecurity market. The bottom of the triangle represents the largest opportunity but also the lowest potential of price per unit. The top of the triangle represents a smaller portion of the market but also the largest price per unit. But the entire triangle, should you have a product to address every market area, represents tremendous potential. Selling into the triangle is something made possible by a combination of CertNexus and Logical Operations offerings with the most important takeaway being that you can address your customers’ every need.
|

|
General Population. This group spans an entire organization and is made up of information workers --- people who use technology devices every day in the normal course of doing their jobs. Because the computers and other devices they use are connected to networks, and ultimately the Internet, this group poses the single largest risk for a breach. CyberSAFE teaches the basics of cybersecurity and the behaviors every information worker can embrace to create a more cyber-secure organization.
IT Applications. Application Developers build websites and applications that sit on a network. Their tools of choice are languages like HTML, Python, Java, JavaScript, C, C#, and many others. They build the apps that allow us to order food and conduct banking from our computer or cell phone. Apps built by developers without a “security-first mindset” can create significant risk. Cyber Secure Coder (CSC) teaches principles and practices every developer can employ, regardless of the language they use, to ensure that the applications they bring to market are secure by design.
IT Operations. When you mention cybersecurity to the average person, they think about it as the domain of the teams that manage the IT infrastructure --- switches and routers, Internet connections and networks, and devices connected to those networks. This is true. These are the people that most of us rely on to spot, isolate, mitigate, recover, and protect from hackers. The NIST (National Institute of Standards and Technology) 800-171 framework is broadly accepted as the guiding standard for cybersecurity and CFR-410 maps to that standard by teaching IT professionals how to identify, protect against, detect, respond to, and recover from cyber threats.
>Cyber Leaders. These are the people responsible for the strategy, implementation, and management of the security framework. They guide and govern the cybersecurity of the organization they work for and are relied upon to ensure that data and systems are safe from breaches. From the Chief Information Security Officer (CISO) to the IT Team Leader, these managers must maintain and continuously optimize the cybersecurity posture of their organization. Certified Information Security Manager (CISM) teaches the foundations of managing cybersecurity programs and cybersecurity teams. Certified Information Systems Auditor (CISA) teaches IT professionals the auditing skills necessary to ensure cybersecurity programs and policies are well managed. And Certified Information Systems Security Professional (CISSP) teaches the eight security domains that comprise the Common Body of Knowledge --- skills and understanding necessary to lead and evolve a cybersecurity program.
As you work with your customers and explore what type of cybersecurity training they need, think about the triangle. Address the information workers’ needs with CyberSAFE, the Application Developers’ needs with CSC, the IT Operations’ needs with CFR, and the IT cybersecurity leaders’ needs with CISA, CISM, and CISSP. I can assure you that breaking down the market and the sales opportunities using this model will address 95% of the cybersecurity training needs of any organization.
|
|
|
|
|
Even Better Protection with CyberSAFE: Exam CBS-410
by Pam Taylor, Senior Instructional Designer
|
| |
|
 The cybersecurity landscape is ever-changing, and new threats seem to emerge almost every day. Security professionals make a point to be aware of new threats and how to counteract them. But how about the people who use technology to do their jobs without being tech pros? CyberSAFE is designed to give everyone a fighting chance against cybersecurity threats. The cybersecurity landscape is ever-changing, and new threats seem to emerge almost every day. Security professionals make a point to be aware of new threats and how to counteract them. But how about the people who use technology to do their jobs without being tech pros? CyberSAFE is designed to give everyone a fighting chance against cybersecurity threats.
A new version of CyberSAFE is arriving soon, and Logical Operations, in partnership with CertNexus, is excited to offer updated instructor-led training for this popular cybersecurity credential. The new CBS-410 courseware is quite like its predecessor, with a few important changes to be aware of.
As with other courses developed to support certification credentials, an update to the CBS-310 exam and blueprint is the driving factor behind the new version of the CyberSAFE course. The CBS-410 exam and blueprint contain new content to address emerging threats. Most notable is a change to the Online Security domain that addresses the critical current issue of cybersafety when working remotely.
Other significant changes include an increased emphasis on compliance requirements and expanded coverage of authentication factors. All these changes are reflected in the CyberSAFE: Exam CBS-410 course, along with additions and updates to course activities to cover the new content. These changes provide learners with current, relevant information, enabling them to protect their devices and data and their company’s data and other resources.
We also took this opportunity to update the look and feel of the slide decks and visuals. Slide decks are now in widescreen format, with more visually engaging slides and fewer text-heavy slides. Visuals are based on a consistent icon set that employs the CertNexus color palette. We feel these changes can enhance your presentation of the material, resulting in learners absorbing more information during training events.
As Megan Smith Branch mentioned in the November 2021 edition of Logically Speaking, the team assembled for the updated CBS-410 blueprint and exam is a diverse one. Contributors from around the world gathered virtually to discuss and update the existing blueprint. To provide a solid link between the CBS-410 updates and our course updates, we invited Shinesa Cambric to act as SME for the course as well. In fact, the entire project team for the course update is female!
For more information about the CBS-410 credential and the CyberSAFE: Exam CBS-410 course, visit https://certnexus.com/certification/cybersafe/.
|
|
|
________________________________________
|
|
|
Our Cybersecurity Curriculum – Developed and Shaped by Women
by Nancy Curtis, VP, Content
|
| |
|
 Since Logical Operations’ original founding as a technology training center and technical curriculum publisher forty years ago, women have been leading contributors to our suite of products. That has always included the most advanced and cutting-edge materials in high tech, emerging tech, and cybersecurity. Since Logical Operations’ original founding as a technology training center and technical curriculum publisher forty years ago, women have been leading contributors to our suite of products. That has always included the most advanced and cutting-edge materials in high tech, emerging tech, and cybersecurity.
Marrying this issue’s twin themes of cybersecurity and International Women’s Day, here are a few notes on some of the important, current Logical Operations and CertNexus cybersecurity curriculum products that have been driven by primarily female creative teams.
-
Certified Information Systems Security Professional (CISSP®): CISSP has long been considered an elite cybersecurity certification, and Logical Operations has published several popular editions of CISSP curriculum to assist certification candidates in their preparation. There have been many important female contributors to the CISSP curriculum over time, including LO instructional designers Pam Taylor and Tamara Hagen, as well as trainer, networking professional, and cybersecurity consultant Chrys Thorsen.
-
Cybersecurity Maturity Model Certification (CMMC): This important security assessment program from the United States Department of Defense (DoD) will require a highly trained body of certified cybersecurity assessors and other CMMC professionals. LO is one of a limited number of organizations that the CMMC Accreditation Body (CMMC-AB) has designated as a Licensed Partner Publisher (LPP), and one of only three LPPs currently approved to release CMMC-AB Approved Training Materials (CATM). The core of the CMMC curriculum development group at LO is female; instructional designers Laurie Perry and Tamara Hagen work tirelessly as a team with our distinguished subject matter experts Tara Lemieux and Amy Coddens (featured in this issue) to bring this critical component of our nation’s security defenses to fruition.
-
CyberSAFE: Exam CBS-410: As you read earlier in this issue, the most important zone of security in any organization or enterprise is between the user and the desktop or device. CyberSAFE 410 was a collaborative effort between LO instructional designer Pam Taylor and CNX cybersecurity consultant Shinesa Cambric. We think you’ll agree that this latest iteration of CertNexus’ CyberSAFE training and credential is the strongest and most effective CyberSAFE yet, and a critical component of any organization’s cybersecurity defenses.
And of course, it’s not just security - women are key contributors in all development roles to the entirety of the LO and CNX curriculum lines. Check out our product listings today.
|
|
|
|
________________________________________
|
|
|
________________________________________
|
| Latest Product Highlights |
| |
|
|
|
|
|
|
________________________________________
|
LogicalLAB Duration Changes for 2022
by Nancy Curtis, VP, Content
|
| |
|
 At the beginning of 2022, our LogicalLAB hosting partner, Skillable (formerly Learn On Demand Systems) changed how lab duration times are calculated and enforced within the Skillable system. On the plus side, duration restrictions like this help to ensure that there are always sufficient Skillable system resources at any time, by limiting labs that might be running but inactive. At the beginning of 2022, our LogicalLAB hosting partner, Skillable (formerly Learn On Demand Systems) changed how lab duration times are calculated and enforced within the Skillable system. On the plus side, duration restrictions like this help to ensure that there are always sufficient Skillable system resources at any time, by limiting labs that might be running but inactive.
The effect on user experience of Skillable’s change is to reduce the total time that a LogicalLAB can run during an individual session. Previously, you could extend a lab as much as needed – even up to a full day. Now, there is a hard maximum, which includes any extensions of the original LogicalLAB session, as well as any time spent after re-launching a saved LogicalLAB. After the session times out, users must exit and re-launch the profile if they want to continue.
To balance this new system restriction, Logical Operations has configured longer durations for the majority of our LogicalLAB portfolio. Now, the expected duration of a given LogicalLAB will always exceed the projected teaching time in the companion CHOICE courseware manual. And, you’ll be able to extend that new, longer, baseline duration by an additional 50% if needed.
The effect of Logical Operations’ updates should be that you and your learners have a generous amount of access time for each LogicalLAB profile. A side effect of the change is that the expected times on the LogicalLAB launch screens might look a lot longer than the course itself! Don’t be surprised by that - it’s all to ensure that you have the access you need to accomplish your instructional goals.
|
|
|
________________________________________
|
|
Content Revisions
|
|
Logical Operations revises student and instructor materials based on technical changes, customer feedback, and our own assessment of necessary changes. The revision notes for the most recent updates are below as well as posted on the Content Revisions page. Use this page as a resource to quickly access and view all revision details for any of our recent course updates.
Reminder: When viewing a product on the store, check the Revision Information tab to see the summary description of the most recent revision for that product at any time.
|
|
|
|
|
Over 125,000 Trained from a $50 Start-Up Investment:
An Interview with Terri Williams Davy, COO
by Jim Gabalski, VP, Sales and Marketing
 It was 1988 when Thelma Tippie got the news that she had been laid off due to downsizing from a very good job. With a $50 deposit, grit, determination, and confidence in the computer training skills she had honed at her former employer, she started The Computer Workshop as a faith-based, family-owned business and the only woman-owned IT Training company in Columbus, Ohio. Joining Thelma in the business are her son and two daughters: David Willams (Vice President), Kim McFarland (Chief Financial Officer), and Terri Williams Davy (Chief Operating Officer), who was interviewed for this Spotlight. It was 1988 when Thelma Tippie got the news that she had been laid off due to downsizing from a very good job. With a $50 deposit, grit, determination, and confidence in the computer training skills she had honed at her former employer, she started The Computer Workshop as a faith-based, family-owned business and the only woman-owned IT Training company in Columbus, Ohio. Joining Thelma in the business are her son and two daughters: David Willams (Vice President), Kim McFarland (Chief Financial Officer), and Terri Williams Davy (Chief Operating Officer), who was interviewed for this Spotlight.
|

The Computer Workshop family
includes (from left to right) Kim, Terri,
Thelma,
and David
|
| |
|
When you speak with Terri, the word “values” comes screaming into your mind. While the business is run on sound practices including minimal debt, organic growth, and driving reinvestment from retained earnings, it’s the human values that really leave you impressed with The Computer Workshop’s story. Successfully navigating the nuances of providing training to people from government agencies, large corporations, small companies, organized labor, and not-for-profits, this faith-based training provider takes great pride in providing training to those who otherwise would not have access. The Computer Workshop is actively involved in the Columbus community, sponsoring/supporting soup kitchens, 4H Clubs, Churches, “Cool Tech Girls” programs for middle schoolers, and homeless initiatives; they do it with the same vigor that they bring to providing training to IT professionals in Columbus and around the world.
“On a daily basis, I hear from students we’ve trained that we helped them get new jobs or get a promotion or enter a new field that they are passionate about," says Terri, adding “That is a very satisfying feeling." The Computer Workshop operates like an extended family with many employees spending a decade or more as part of the team. “An employee of nearly 20 years recently moved on to an exciting new role with a different organization," said Terri, “She was part of the family and I feel like she grew up here. While we were sad to see her leave, she will always be part of The Computer Workshop family." Terri also takes great pride in training quality and the resilience of the company. “We started in desktop applications, added in Networking, then Programming, Cloud, Cybersecurity, Blockchain, and other leading-edge technology as the industry demands. We continue to answer the market needs but always ensure we are using or creating world-class content.”
So, what’s next for The Computer Workshop? Already heavily invested in data training, they’ve selected courses to teach that ensure best-in-class training for Data Analysts and Data Scientists. They have created a Storytelling With Data course that Terri says is “one of our hottest classes.” Recognizing that the COVID Pandemic created a pivot point in the training industry, Terri and her team are asking some important questions. Is in-person training coming back? Will it continue to be virtual as the dominant delivery modality? Will the Metaverse change everything? Am I going to accept Bitcoin for payment? But regardless of the answers to those questions, Terri is confident that the backbone of The Computer Workshop will remain --- People. Confident that people will always learn best from people, great customer service will never go out of style, and that service to the community is always the right thing to do, everything else will take care of itself.
“My 83-year-old Aunt Barb Leatherwood came to work with us 10 years ago,” said Terri. “She never wanted to work with a computer but we set one on her desk. The second day on the job she asked how to work it so we got her going. Now she wants a THIRD screen!” The Computer Workshop changes lives!
Terri’s advice, “Walk slowly. Listen. Be kind.” Great words to live by.
|
|
|
|
|
|
|
|
|
Don't Leave $1B+ in Training Opportunity on the Table
|
| |
CMMC 2.0 creates more than one billion dollars in training potential. Learn how to take advantage of this huge opportunity with Jedi Jon's recent CMMC 2.0 Tech Talk. He covers:
- A brief background on CMMC 2.0
- Course(s) you can teach to take advantage of the CMMC opportunity
- Target organizations and job titles
- Common questions to start with
- Overcoming objections
Watch the CMMC 2.0 Tech Talk recording now.
|
|
|
|
|
March 2022 Instructor Excellence Award: Amy Starzynski Coddens
|

Amy Starzynski Coddens
CMMC CCP Instructor
and Strategic Partnerships Manager
Research and Education Networks
Information Sharing and Analysis Center
(REN-ISAC) |
|
|
| |
|
|
|
Amy Starzynski Coddens is a CMMC CCP instructor who currently serves as the Strategic Partnerships Manager for the Research and Education Networks Information Sharing and Analysis Center (REN-ISAC). “I’m kind of a Swiss Army knife of education/outreach skills & knowledge with a dash of cybersecurity thrown in.” Amy came to the REN-ISAC from Indiana University's Center for Applied Cybersecurity Research, where she served as the Education, Outreach, and Training Manager, but she has a background in P-16 education, research, and outreach. Having experience working with the government and in academia, Amy has contributed to projects with the CMMC-Accreditation Body, National Science Foundation, NASA Education, the New England Research Institute, Harvard’s PEAR Institute, the United States Department of Education’s Office of Special Education Programs, and the IU Kelley School of Business.
Before focusing on CMMC CCP training, Amy taught everything from Behavior Management to children's yoga. According to Amy, she was originally drawn to CMMC because it was something new and kind of mysterious at the time. “I kept learning about it and truly became passionate about the model and how each part of the ecosystem fits and matters once I became more aware of the 'why' around its creation. No, I don't think it's perfect, but I do think it is needed. I also think the fact that POA&Ms are allowed in version 2.0 is a very good thing!”
Amy comes from a long line of educators, so she feels like she always wanted to be a teacher. Amy never strayed away from education and got her B.S. in Public Health Education but wasn’t always involved in direct instruction. “I am an extrovert and can talk to people all day long about nothing. I did love being in the classroom, but it wasn't really for me. Instructing adults, however, gives me the best of both worlds.” Although Amy enjoys every part of her job, a part that stands out to her is finding a way to easily explain difficult concepts so they are easily understood. “I used to teach special education a few lifetimes ago, and I have the view that approaching teaching and learning as something that is moving/breathing/living and CAN be changed to fit each student is a pretty good philosophy. It's all just like a giant puzzle - you just have to figure out where the pieces fit!”
This past year, Amy has been fortunate enough to serve with a group of other amazing women to stand up the Women in Cybersecurity (WiCyS) Business Information Security Officer (BISO) Affiliate. The BISO role is relatively new but is one that is projected to open up a career track for women in the field of cybersecurity. Looking to the future, Amy would absolutely love to move into more of a leadership role, but also truly loves the work that she does at the REN currently. “Every day is different, I get to work with amazing partners from all over the higher education and research landscape to better security awareness, and our team is fantastic. I also enjoy the work I have done with EDUCAUSE, WiCyS, and other organizations - my cup is pretty full!”
As a lifelong Hoosier, Amy is currently working toward a Graduate Certificate in Cybersecurity Law and Policy through the Indiana University Maurer School of Law. She lives in Bloomington, Indiana with her husband, Zachary, who also works in cybersecurity at the OmniSOC (he's more technical and is a security engineer), and her two amazing children, Ellie and Emma.
|
|
|
|
|
|
|
________________________________________
|
March 2022 Instructor Excellence Award: Mike Brown
| |

Mike Brown
Certified Technology Instructor
New Horizons
Computer Learning Centers
|
| |
|
Mike Brown is a Certified Technology Trainer at New Horizons Computer Learning Centers where he teaches technical certification courses including CompTIA, ITIL, and Microsoft System Engineering. Mike has taught an array of classes over his 20 years as an instructor to over 8,500 students. In addition, he has also written his own content and has dozens of courses on platforms like Udemy and Wyzant.
Mike has always been interested in computers. The first computer he ever clicked on was running Windows 3.11. He just naturally took to computers, he says, “It was like I was always meant to be in the computing field, and there came a time when I realized I was good at teaching other people to use their computers!” That day, a computer instructor was born in Mike, and he knew he had to find a job as an instructor and start teaching. “I know this is hard to believe. but I first heard of New Horizons Computer Learning Center by responding to a newspaper ad in the mid-1990s! Yes, so long ago that help-wanted was still in a newspaper!” It would be several years later that Mike would get hired and would conduct his very first class. “I was not going to take no for an answer, I HAD to be a computer instructor! I called and hounded them for 6 months before they finally gave me a position. That was in 2002 and I've been an instructor ever since.”
Mike would not change a thing about his job as an instructor. One of the biggest reasons why he enjoys it is because he feels that you are in control of the class, like a leader, but not a boss. You are a student's motivator, role model, and confidant as they learn new skills and meet their personal goals. “I have been a college professor, taught for the Board of County Commissioners, and worked for years with New Horizons and the best part is that connection when a student learns something new.” Sometimes Mike looks back and thinks about all the lives he has changed over the years. “People that now have college degrees, CompTIA certifications, or students that just wanted a new skill all have been changed forever because I was their instructor. This is what any instructor enjoys about teaching,” Mike says.
Another reason why Mike feels so rewarded in what he does every day is that before he gained his passion for computers, he never even imagined that being an instructor was in the cards for him. “If it wasn't for that time I, almost by divine intervention, came across a tiny PC running Windows 3.11 --- who knows where I would be. I opened Microsoft Paint and started playing with it and now 27 years later, I live a great, happy prosperous life...all because of a series of wildly connected, lucky after lucky, events that brought me to where I am now.”
So, what's next for Mike? Well, in his eyes you can never have too many certifications! So, he is sure he will have many more exams to study for! As a Key Wester, he has his kayak and his dog and a lot of adventures yet to be had. “Wherever I go I know I'll have great students and great content to teach them as long as I use Logical Operations! They are what made me such a great instructor!”
|
|
|
|
|
|
|
________________________________________
|
Submit Your Instructor Nominations for April
 We're recognizing instructors who have reached key milestones and made a meaningful impact in the training world. Do you want to nominate an instructor who you feel deserves to be recognized in the next Logically Speaking? Visit the Instructor Spotlight page to get more insight into what the Instructor Spotlight is all about. We're recognizing instructors who have reached key milestones and made a meaningful impact in the training world. Do you want to nominate an instructor who you feel deserves to be recognized in the next Logically Speaking? Visit the Instructor Spotlight page to get more insight into what the Instructor Spotlight is all about.
|
|
|
|
|
|
|
|
|
|
|
CFR Instructor Tools
by Megan Branch, Chief Operating and Product Officer, CertNexus
 Are you ready to teach CertNexus’ CyberSec First Responder® for the CFR-410 exam? CertNexus has created a set of tools designed for busy instructors who want to add a globally recognized certification course to their portfolio. Each instructor bundle is designed to set you up for success. Are you ready to teach CertNexus’ CyberSec First Responder® for the CFR-410 exam? CertNexus has created a set of tools designed for busy instructors who want to add a globally recognized certification course to their portfolio. Each instructor bundle is designed to set you up for success.
- Instructor curriculum with:
- Notes to assist with content
- Setup instructions
- Scheduling and timing tools
- Train the trainer (TTT) videos.
- Exclusive tips and resources from a Master Instructor.
- Bridge documents and videos for experienced trainers who taught CFR for CFR-310.
- PowerPoints that are customizable to meet the needs of your class.
- Mapping document for students preparing to take the CFR-410 exam.
- Access to Master Instructor via CHOICE messaging.
- Optional lab access.
To learn more about the CFR Instructor Bundle, visit here. |
|
|
|
|
|
|
________________________________________
|
What’s Next: How Do You Answer a Student’s Most Pressing Question?
by Jon O'Keefe, Technology Education Jedi
Picture this: You’ve just finished teaching an entry-level IT course. A student opens their microphone or raises their hand and asks you, “What’s next?”
 It is a question we get asked often, especially in the IT and security space. It’s an exhausting question as we’ve just finished a long class, and it is one that’s easy to brush off and leave to someone else to answer. We must be mindful as instructors that the “What’s Next?” question is a gift, not a burden. It is this question that can help shape not only the careers of our students, but also our own as well. There are literally hundreds of certifications out there in the IT space, and students will get conflicting information from Reddit, co-workers, and YouTube in the coming days and weeks after your class. However, not all of those lead directly back to you and your organization, and this one question of “What’s Next?” is the best opportunity you have to keep your students coming back for more. It is a question we get asked often, especially in the IT and security space. It’s an exhausting question as we’ve just finished a long class, and it is one that’s easy to brush off and leave to someone else to answer. We must be mindful as instructors that the “What’s Next?” question is a gift, not a burden. It is this question that can help shape not only the careers of our students, but also our own as well. There are literally hundreds of certifications out there in the IT space, and students will get conflicting information from Reddit, co-workers, and YouTube in the coming days and weeks after your class. However, not all of those lead directly back to you and your organization, and this one question of “What’s Next?” is the best opportunity you have to keep your students coming back for more.
Recommending the “next class” can be a huge responsibility, however. This is why you need to have a plan and a path forward. Make sure you can recommend the next steps from basic to intermediate, to advanced, and even to specialized vendor certifications. Logical Operations includes a whole “What’s Next” section at the end of all of our courseware to give you and the students some ideas on how to continue along their journey. At the end of any class, you should always be prepared to show the next few classes/certifications your students should be looking to earn (bonus points if you can teach these as well, for your own income and job security).
Don’t treat the end of the class question of “What’s Next?” as a burden, and instead prepare to answer it for any class that you teach. Logical Operations and CertNexus believe there is always more to learn, and so we provide some ideas in a “What’s Next” section at the end of every CHOICE manual. Your students will be more likely to return to take classes from you if you spend a few extra minutes at the end of your class to show them the path forward.
|
|
|
|
|
|
|
|
|
|
|
Searching the Logical Operations Store Made Easy with These Steps!
by Chandra Foster, VP, Global Client Services
Looking for security material such as CFR-410?
URL: https://store.logicaloperations.com/
With each selection, it reduces the list of products for ease of ordering.
Now, you have two options for Student Digital material: one with lab and one without. Select ADD TO CART.
It’s that simple!
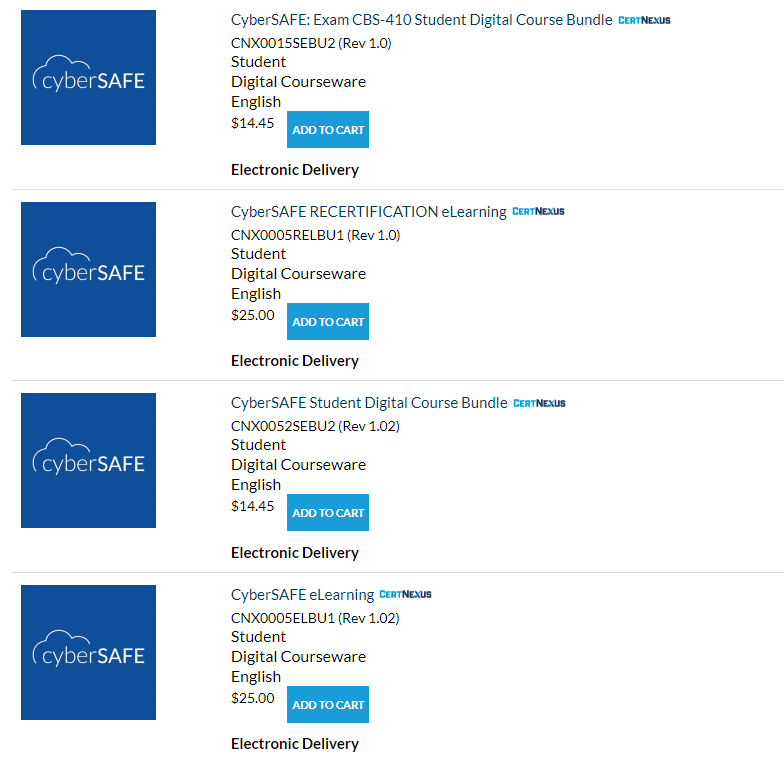
The same can be done with CyberSAFE:
The four courses are below. Those who are already certified and need to stay in compliance would order the CyberSAFE RECERTIFICATION eLearning course. The other options are the standard CyberSAFE course or the eLearning version, if preferred.
As always, the Assist Team is here to help. We can be reached at assist@logicaloperations.com or 1-800-456-4677 option 2.
Chandra Foster
VP, Global Client Services
assist@logicaloperations.com
1-800-456-4677 option 2
|
|
|
|
|
|
|
|
|
|
|
Inside LO - Powered by the Experience of Women
by Nancy Curtis, VP, Content
| |
|

|
| |
|
As the Logical Operations staff member with the longest continuous tenure with the company (31 years), I can personally attest to the importance of all my female colleagues in driving the success and shaping the culture of LO and its predecessor companies. LO has always been a place where female professionals in any job role can thrive and succeed in an atmosphere that not only welcomes but embraces women’s perspectives, concerns, needs, and points of view.
Currently, women make up about half of the total employee base of the LO family of companies (including CertNexus, New Horizons@LO, and Logical Operations itself). We have female leaders and contributors on all levels and in all areas of the company, including my own Content group, the Client Services and Finance teams, as well as Partners, Sales, and Marketing. CertNexus is 75% female!
The LO family is a relatively small and tight-knit group, so it’s amazing to realize that the strong women across the team have a total of nearly two and a half centuries of experience with the company (243 years to be exact)!
Here's what some of my other long-tenured colleagues have to say:
|
Barely in my 30s when I joined LO, I had no idea this career would take me through the rest of my working years. From the start, it was evident that women and all employees were encouraged to develop, grow, and expand their technology skills. The connection between learning and helping others learn was baked into every project. I can’t imagine anywhere else that provides the fulfillment of creating learning experiences that help others change and succeed. -Pam Taylor, Senior Instructional Designer, Content (31 years)
|
|
I’ve been promoted from entry-level to senior leadership within a company that values women as much as the men; in fact, I’ve never had to think about it. That says a lot about how our company is run. -Chandra Foster, VP, Client Services (27 years)
|
|
LO/CNX (since I have now had the opportunity to work for both!) is not an environment you come across often in a career. Therefore, you work diligently amidst the roadblocks and challenges, grow in failures, and display gratitude in ways that honor International Women’s Day personally, professionally, and globally. Every day. -Andrea Bucklaew, Certification Development Manager, CertNexus (24 years)
|
|
What I’ve always liked is that there’s never a dull moment. 22 years at the same company never made me feel like I was in a rut, because things constantly changed and there was always something new. -Sherry Crittenden, Credit Analyst, Finance (22 years)
|
I couldn’t agree more with my colleagues. I’ve also benefited from LO’s gender-equitable technical and professional advancement, as well as the extraordinary flexibility the company provided for me to raise and support a family as a full-time working woman. Thanks to everyone at LO for building and maintaining a community that values each employee’s authentic self.
|
|
|
|
|
|
|

 We are living through a “Perfect Storm” of events for individuals who want to pursue cybersecurity careers. With the skills gap already worsening, many security professionals retiring or looking for other opportunities, and the new face of war being a potential massive cyber conflict, there has never been a better time to invest in your growth as a cybersecurity professional. If you look at all of that and combine it with the fact that fewer young people are going to college in lieu of getting vocational/certification training, you have the conditions for an explosion in cybersecurity training.
We are living through a “Perfect Storm” of events for individuals who want to pursue cybersecurity careers. With the skills gap already worsening, many security professionals retiring or looking for other opportunities, and the new face of war being a potential massive cyber conflict, there has never been a better time to invest in your growth as a cybersecurity professional. If you look at all of that and combine it with the fact that fewer young people are going to college in lieu of getting vocational/certification training, you have the conditions for an explosion in cybersecurity training. 


 The cybersecurity landscape is ever-changing, and new threats seem to emerge almost every day. Security professionals make a point to be aware of new threats and how to counteract them. But how about the people who use technology to do their jobs without being tech pros? CyberSAFE is designed to give everyone a fighting chance against cybersecurity threats.
The cybersecurity landscape is ever-changing, and new threats seem to emerge almost every day. Security professionals make a point to be aware of new threats and how to counteract them. But how about the people who use technology to do their jobs without being tech pros? CyberSAFE is designed to give everyone a fighting chance against cybersecurity threats.  Since Logical Operations’ original founding as a technology training center and technical curriculum publisher forty years ago, women have been leading contributors to our suite of products. That has always included the most advanced and cutting-edge materials in high tech, emerging tech, and cybersecurity.
Since Logical Operations’ original founding as a technology training center and technical curriculum publisher forty years ago, women have been leading contributors to our suite of products. That has always included the most advanced and cutting-edge materials in high tech, emerging tech, and cybersecurity.  Join the
Join the 









 Are you ready to teach CertNexus’ CyberSec First Responder® for the CFR-410 exam? CertNexus has created a set of tools designed for busy instructors who want to add a globally recognized certification course to their portfolio. Each instructor bundle is designed to set you up for success.
Are you ready to teach CertNexus’ CyberSec First Responder® for the CFR-410 exam? CertNexus has created a set of tools designed for busy instructors who want to add a globally recognized certification course to their portfolio. Each instructor bundle is designed to set you up for success.  It is a question we get asked often, especially in the IT and security space. It’s an exhausting question as we’ve just finished a long class, and it is one that’s easy to brush off and leave to someone else to answer. We must be mindful as instructors that the “What’s Next?” question is a gift, not a burden. It is this question that can help shape not only the careers of our students, but also our own as well. There are literally hundreds of certifications out there in the IT space, and students will get conflicting information from Reddit, co-workers, and YouTube in the coming days and weeks after your class. However, not all of those lead directly back to you and your organization, and this one question of “What’s Next?” is the best opportunity you have to keep your students coming back for more.
It is a question we get asked often, especially in the IT and security space. It’s an exhausting question as we’ve just finished a long class, and it is one that’s easy to brush off and leave to someone else to answer. We must be mindful as instructors that the “What’s Next?” question is a gift, not a burden. It is this question that can help shape not only the careers of our students, but also our own as well. There are literally hundreds of certifications out there in the IT space, and students will get conflicting information from Reddit, co-workers, and YouTube in the coming days and weeks after your class. However, not all of those lead directly back to you and your organization, and this one question of “What’s Next?” is the best opportunity you have to keep your students coming back for more.