
As cyber threats continue to grow and ransomware attackers are more emboldened, the best defense is an organization that thinks “security” first, at all levels. The best approach to building a security-first culture is providing the right type of training to the right audience. The Logical Operations ALIAS —All Levels Information Technology & Application Security — training program is designed to create a security-first mindset throughout an organization. Explore training for each role.
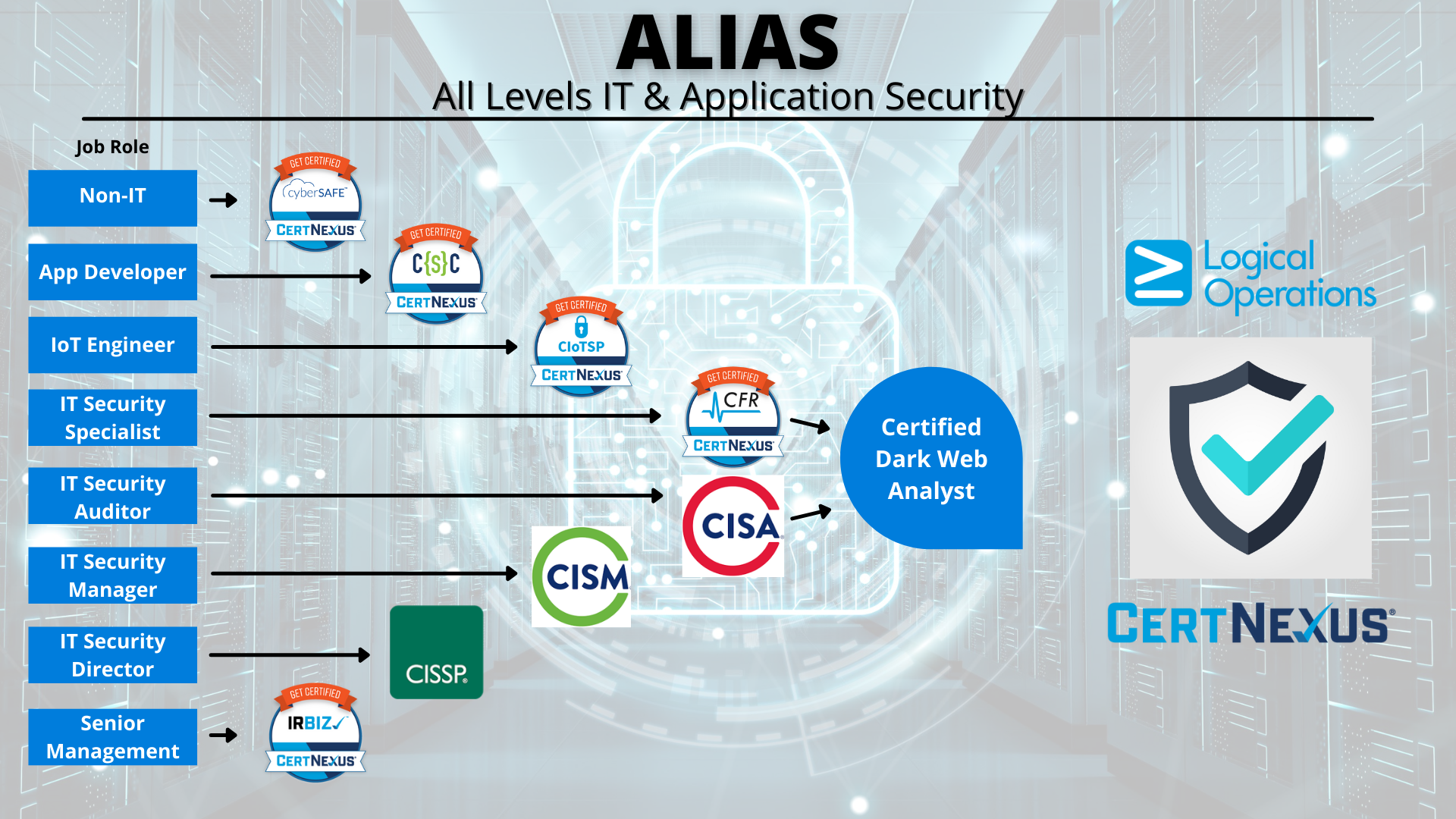
Job Role |
Best Fit Training |
|
Non-IT, General Worker |
CertNexus CyberSAFE: This group of people do not specialize in information technology but represent the largest population of trainees. They are also the weakest link and the likely target of most security threats. CyberSAFE teaches basic behavioral modifications that will significantly reduce a company’s risk of breach. |
|
Application Developer |
CertNexus Cyber Secure Coder (CSC): Application developers create tools that businesses and customers use, such as a website. Security by design principles taught in CSC can be applied to any development language and, when put into practice by the Application Developer, close “common holes” left in applications that hackers exploit. |
|
IoT Engineer/Developer |
CertNexus Certified Internet of Things Security Practitioner (CIoTSP): As many companies engineer and deploy IoT applications that leverage customer networks and the Internet, security risks increase exponentially. CIoTSP, or Certified IoT Security Practitioner, teaches how to build IoT applications that are secure. Imagine what could happen if someone hacked your IoT-enabled Smart TV. |
|
IT Security Specialist |
CertNexus CyberSec First Responder (CFR) and Certified Dark Web Analyst (CDWA): The Security Specialist is on the front line and will likely be the First Responder when a breach occurs, and they will occur. CyberSec First Responder teaches the IT Professional how to Identify, Isolate, Remediate, and Prevent future occurrences of a threat. Certified Dark Web Analyst training teaches how to safely use the Dark Web to identify pending threats by “listening in” on hacker conversations. It also provides instruction on how to prepare data for recovery in the event it is exfiltrated. And finally, CDWA teaches how to actually recover data. |
|
IT Security Auditor |
ISACA Certified Information Systems Auditor (CISA) and Certified Dark Web Analyst (CDWA): Security Auditors review breaches and threats and determine the best course of action to reduce risk of future threats. Certified Information Systems Auditor (CISA) teaches the IT auditor how to assess information systems, security controls, and vulnerabilities with improvement or “hardening” of systems’ security as the focus. CDWA provides the CISA candidate with access to “what the bad guys are talking about”. Taking this course will provide the Auditor with the skills needed to identify pending threats to audit systems against. |
|
IT Security Manager |
ISACA Certified Information Security Manager (CISM): IT Professionals in management positions that include management of security professionals and/or processes require skills specific to the topic of security management. Certified Information Security Manager (CISM) is aimed at those professionals and prepares the candidate to sit for the ISACA CISM Certification Exam. |
|
IT Security Director |
(ISC)² Certified Information Systems Security Professional (CISSP): The Security Director sets strategy and policy for IT security within an organization. Certified Information Systems Security Professional expands the knowledge of the candidate by exploring the essentials of each of the 8 domains of the Common Body of Knowledge for information systems security professionals, preparing them for leadership and policy setting roles. |
|
Senior Management |
CertNexus IRBIZ: Senior Managers just need the basics. Incident Response for Business Professionals provides just that. Company executives and senior leaders are ultimately responsible for complying with incident response legislation. This course focuses on the knowledge, resources, and skills necessary to comply with incident response and incident handling process requirements. |
Questions? Want a free evaluation copy of any of the courses in the ALIAS training program? Fill out the form below and we'll reach out to you.
↓


