|
Welcome to the October edition of Logically Speaking! In honor of National Cybersecurity Awareness Month, this issue focuses on cybersecurity training and what you need to know right now.
We hope you enjoy it and welcome any feedback.
In this issue:
.
|
|
|
|
|
|
|
|
|
|
CMMC: The Next Big Training Opportunity
by Jon O'Keefe, Technology Education Jedi
 |
Jon O'Keefe
Technology Education
Jedi |
The Cybersecurity Maturity Model Certification (CMMC) represents one of the largest areas of growth for training providers in cybersecurity. With over 350,000 organizations, plus millions of subcontractors currently standing by to receive training in CMMC, the opportunity is not only around specific CMMC training, but also other areas of cybersecurity and compliance. This amounts to about $1.5 BILLION of training that will need to happen globally over the next two years. Are you ready?
There are two paths to offering CMMC training and Logical Operations can help you with both:
- Become a Licensed Training Provider with the cyberab.org, and be able to offer AUTHORIZED CMMC CCP training to individuals who want to become assessment professionals and to organizations who want to certify internal employees. Logical Operations is a Licensed Publishing Partner (LPP) and can provide you with Official content once / if you become an LTP.
- Offer UNAUTHORIZED training through Logical Operations’ CMMC Boot Camp, which can be used by any person who does not want to achieve a CMMC certification but does want to learn all about CMMC.
Want to learn more about CMMC? Check out https://cmmclpp.com.
Whichever path you choose for offering CMMC training, we can assist you. Here is a list of individuals who might need CMMC training (either authorized or unauthorized):
- Employees of Organizations Seeking CMMC Certification (OSCs)
- Information Technology (IT) and Cybersecurity Professionals
- Regulatory Compliance Officers
- Legal and Contract Compliance Professionals
- Management Professionals
- Cybersecurity and Technology Consultants
- Federal Employees
- Candidate CMMC Assessment Team Members
There are other opportunities that surround CMMC that many organizations will be looking to take advantage of. CMMC is all about cybersecurity and resilience, and specific parts of CMMC point towards cyber compliance training, incident response training, and coding and patching procedures.
We offer CyberSAFE (compliance), CyberSec First Responder (incident response), and Cyber Secure Coder (coding) as well as many other cybersecurity courses that can help your customers feel prepared for their CMMC assessments.
With billions of dollars opportunity, now is the time to offer CMMC training to your clients before someone else does. Contact sales@logicaloperations.com to get started!
|
|
|
|
|
|
|
|
|
The Rise of Cybersecurity Insurance and CyberSAFE Training
by Jon O'Keefe, Technology Education Jedi
|
| |
 |
Jon O'Keefe
Technology Education
Jedi |
In the next five years, every organization will be training their non-IT employees in basic cyber resiliency and awareness. There are three factors driving organizations towards this:
- The rise of cyber insurance
- Increasing compliance mandates
- The evolving threat landscape
Cyber insurance is growing due to the complex nature of remediating cyber-attacks. According to IBM, the average cost of remediating a breach is 1.7 million USD. These costs are leading organizations to invest in cyber insurance. According to Fortune Business Insights™, Cybersecurity Insurance market size in the United States is expected to rise to 36.85 billion dollars by 2028. That is a growth rate of over 25% year over year.
Cyber insurance companies have started including end-user, cyber resiliency and awareness training requirements into their contracts. For some organizations, being able to demonstrate training will lead to lower premiums, and for others, it will be required before they can submit a claim for a data breach. When you have large amounts of money on the table, organizations will be queuing up to get whatever training that will help them to be in compliance with their insurance policies.
Speaking of compliance, global regulations address the need to train end users in basic cyber resiliency and awareness. There are many local and country-wide regulations that speak to this, such as CMMC and GDPR. Inside of the Defense Industrial Base, NIST 800-171 3.2.1 calls specifically for end-user training on a variety of cybersecurity topics in order to be compliant. New York State also requires all state employees to demonstrate basic cyber awareness on an annual basis. This is becoming more commonplace as the threat landscape evolves to focus more on end users than IT systems.
This brings us to point number 3, the evolving threat landscape. In the past ten years, we’ve seen a rise of social engineering and other types of attacks that specifically target the end user. According to Tech Radar, 90% of all cyber breaches are caused by end-user error. Organizations are suffering breaches because an end user is clicking on an email link or downloading an attachment, or because they are being socially engineered through a variety of sophisticated, and sometimes not so sophisticated, attacks. The end user is now the attack vector by which bad actors are taking advantage of.
All of this leads to the rise of compliance and end-user awareness/resiliency training for your customers. They will be looking for assistance in delivering specific and organization-wide training that is quick, easy for the end user to understand, and has reporting metrics for meeting compliance mandates.
Thankfully, Logical Operations and CertNexus have the solution your customers are looking for. CyberSAFE can address the three points above and is simple to deliver in both an ILT and eLearning format. If any of your customers have expressed concerns about the above topics, you now have access to the solution for them. Contact sales@logicaloperations.com to learn more!
|
|
|
|
|
CMMC: Have It Your Way
by Jon O'Keefe, Technology Education Jedi
|
| |
 |
Jon O'Keefe
Technology Education
Jedi |
The Cybersecurity Maturity Model Certification (CMMC) is going to drastically change the way over 350,000 organizations bid on Department of Defense (DoD) contracts. These organizations, commonly referred to as the Defense Industrial Base (DIB), make up the DoD supply chain along with millions of subcontractors who work underneath them.
The training opportunity is huge, as organizations will need both team members who have achieved certifications in CMMC, as well as team members who have sufficient training in all things related to CMMC.
There are two avenues to participate in CMMC training:
-
Become an Authorized Licensed Training Provider (LTP) through The Cyber AB and offer authorized training on CMMC that leads to specific certifications.
-
Utilize our CMMC CCP Boot Camp courseware for training when individuals or organizations are seeking CMMC knowledge but DO NOT NEED the CMMC certifications.
Logical Operations is a Licensed Partner Publisher (LPP) inside of the CMMC ecosystem and can help you with either pathway. We have both CMMC Authorized Training Materials for existing and new LTPs inside of the CMMC ecosystem, as well as the CMMC CCP Boot Camp for organizations who want to offer the training to clients who do not need/want the CMMC certification.
Depending on your typical audience, either path might be great for you whether you service or are planning on offering training to the following groups of people:
- Employees of the Defense Industrial Base (Information Technology (IT) and Cybersecurity Professionals, Regulatory Compliance Officers, Legal and Contract Compliance Professionals, and Management Professionals)
- Cybersecurity and Technology Consultants
- Federal Employees
- Candidate CMMC Assessment Team Members
With so many needing some form of training on this topic, this remains one of the largest opportunities globally for training in the next few years.
Whether you want to do certification training or knowledge training, Logical Operations can guide you in the right direction. Contact sales@logicaloperations.com with any questions, and we will get you set up with everything you need!
|
|
|
________________________________________
|
|
|
Latest Product Highlights
|
| |
|
Reminder: The CertNexus CyberSAFE: Exam CBS-410 eLearning is available!
It includes everything a student needs to be CyberSAFE: eLearning to become more aware of technology-related risks plus the assessment and credential. Shop the CyberSAFE: Exam CBS-410 eLearning now.
|
|
|
|
|
________________________________________
|
|
|
Content Revisions
|
| |
|
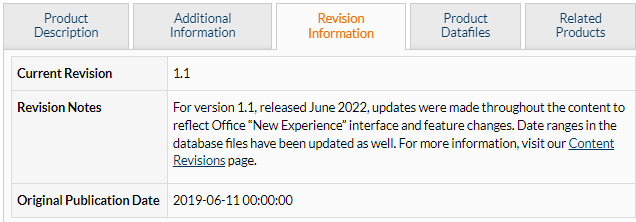
Logical Operations revises student and instructor materials based on technical changes, customer feedback, and our own assessment of necessary changes. The revision notes for the most recent updates are below as well as posted on the Content Revisions page. Use this page as a resource to quickly access and view all revision details for any of our recent course updates.
Reminder: When viewing a product on the store, check the Revision Information tab to see the summary description of the most recent revision for that product at any time.
 /> /> |
|
|
|
|
|
Cybersecurity Around the Globe: The Common Thread
by Jeff Felice, President, CertNexus, and Megan Smith Branch, Chief Operating and Product Officer, CertNexus
 |
Jeff Felice
President,
CertNexus |
 |
Megan Smith Branch
Chief Operating and
Product Officer
CertNexus |
While we may diverge culturally, politically, and geographically, cybersecurity is one issue affecting every person, organization, and country globally. Across the globe, there are multitudes of cybersecurity risk frameworks from organizations such as CIISEC (Chartered Institute of Information Security), NIST (National Institute of Standards and Technology (NIST)), CIS (Center for Internet Security), ISO/IEC (International Standards Organization/IEC (International Electrotechnical Commission)), and more. If frameworks are implemented, they enable global organizations to create a strong security posture and comply with regulations across multiple regions.
At the core of all frameworks is how to reduce and manage risk. And the single, universal resource requirement is people.
Cybersecurity Ventures tracked cybersecurity roles over the last eight years and found a 350% increase in job openings, with 3.5 million of these roles remaining unfilled. That is enough to fill seats at 70 soccer stadiums. India alone will have 1.5 million job vacancies by 2025. How can organizations tackle such a significant issue? We suggest looking at your resources in two non-traditional ways:
1. Make every employee a cybersecurity “deputy.”
When local municipalities cannot pay for or fill spots in their police forces, they deputize normal citizens to alleviate the pressure on the paid employees to keep the community safe. Organizations can “deputize” their employees with CyberSAFE® and alleviate the pressure of their IT (Information Technology) staff and security teams. CyberSAFE addresses the top 5 cybersecurity risks globally (Phishing, Website Spoofing, Ransomware, Malware, and IoT (Internet of Things) Hacking) and how to reduce risk while working remotely. The annual credential maintains knowledge and skills.
2. Shift-left.
This is the practice of moving testing, quality, and performance evaluation early in the software development process, or shifting to the “left” side of the software development lifecycle. In other words, begin focusing on developers. Frameworks such as the NICE (National Initiative for Cybersecurity Education (NICE)) Cybersecurity Workforce Framework and CIISEC identify tasks within 25+ roles dealing with securing software. Why not focus on securing software at the beginning rather than after deployment where products and services typically harbor security debt? CertNexus’ Cyber Secure Coder® trains and validates the skills necessary to shift-left and reduce risk earlier at the design phase.
We may not solve the cybersecurity skills gap overnight, but by changing perspective, organizations may be able to narrow the gap before they fill that open position.
|
|
|
|
|
|
|
|
|
|
|
|
Need Help Locating a CyberSAFE Course?
by Chandra Foster, VP, Global Client Services
 |
Chandra Foster
VP, Global Client
Services |
Contact the Client Services team! We will assist you in locating the correct product, and we will provide you with an evaluation copy of the material to review before you purchase.
Keep your company safe by following this link to purchase the latest CyberSAFE material: https://store.logicaloperations.com/catalogsearch/result/?q=cybersafe.
Any questions, contact our CyberSAFE support team at assist@logicaloperations.com.
|
|
|
|
|
|
|
|


